Is Your Data Protected in the Quantum Age?

Future-proof your data & documents with Testenium's most Secured Encryption.
Explore Testenium Meta Solutions: Your Fortress in the Quantum Age!
Encryption is the Guard of Your Digital Privacy and FreedomEncryption safeguards your personal details, financial data, and digital conversations against unauthorized access, ensuring your online world remains secure, private, and trusted. As the backbone of digital security, it plays a critical role in maintaining your digital freedom and safety in the interconnected internet era, protecting data across platforms.
$8.64 millionis predicted to be the global annual cost of cybercrime by 2025 *
51%Organizations are planning to increase security investments as a result of a breach *
Over 64%Financial services companies have 1,000+ sensitive files open to every employee *
1 in 7 ChancePublic-key cryptography which we rely today will be broken by quantum computing in 2026 *

Are We Aligned on Encryption
Challenges in the Digital Age?
Explore why traditional encryption solutions fall short.
Feeling Overwhelmed by Encryption Keys?Large environments make encryption a juggling act! Keeping track of keys, who has access, where they're stored, and update them regularly is a constant worry. Losing a key locks you out, while unauthorized access exposes everything!
Is Your Data Ready for the Code-Crackers of Tomorrow?Imagine today's encryption being cracked like yesterday's code. Quantum computers pose a real threat, making your data vulnerable. Is it time to future-proof your encryption.
Does Your Data Security Travel With You?Large companies often juggle a mix of devices - laptops, phones, tablets. Encryption that works on one might not work on another. Imagine data locked away on your phone while you're on the go! Shouldn't your data security be as seamless as your mobile life?
Is Your Data Secure on Both In Transit & at Rest?Data requires comprehensive protection - secure while stored (at rest) and safe during transfer (in transit). Imagine needing different security measures for your data depending on whether it's on a server or traveling across a network. Ever worry your encryption can't handle both?



Do the Above Challenges Sound Familiar?
Then You Should Explore How Testenium Solves Them in Clicks!
Testenium offers automated key management & seamless encryption.
Testenium automates key generation for users, streamlining encryption and decryption without key management. As a browser-accessible, cloud-based solution, implementation is seamless. Using the QRNG seed, Testenium creates unique symmetric encryption keys for robust protection. Post-encryption, Testenium promptly deletes keys to thwart unauthorized access. Leveraging the QRNG seed, Testenium effortlessly generates decryption keys for secure document access and key destruction.
- Say goodbye to manual key management
- Effortless implementation
- Top-tier Protection
- Future-Proof Security
- Seamless Encryption and Decryption
Testenium Shields You from Tomorrow's Threats.
Testenium offers top-notch data protection with advanced encryption keys resistant to future threats, including quantum computers. Utilizing a QRNG seed for added randomness, it generates symmetric keys for encryption, destroying them afterward. Decryption is equally secure, regenerating keys from the same seed. With industry-standard 256-bit AES encryption, (NIST Standard)Testenium ensures data remains unreadable to attackers, providing a future-proof security solution.
- Unbreakable Keys
- Randomized Security
- Automatic key deletion
- Encryption Strength: 256-bit AES (NIST Standard)
Testenium’s virtual Encryption goes wherever you go.
Testenium offers a cloud-based platform accessible from anywhere with an internet connection and any web browser. This eliminates compatibility issues and allows seamless access across devices. Additionally, Testenium provides customizable on-premise deployment options for specific needs. With Testenium, your data security travels with you, offering seamless access, device independence, and customizable solutions to keep your information protected wherever you work.
- Cloud-Based Convenience
- Device Agnostic Security
- Customizable Security Solutions
Testenium ensures full data protection in transit, on rest & beyond.
With Testenium’s unified approach, we store your data securely in our cloud-based system, where uploaded documents are automatically encrypted for on-rest protection. Download encrypted files and keep them protected on your personal storage, or securely send them through Testenium's integrated email service without sharing encryption keys. Testenium automates the key exchange for both parties, ensuring your data remains protected everywhere – in transit, on rest, and beyond.
- Secure Cloud Storage
- Automatic Encryption at Rest
- Zero-Knowledge Secure Share for Data in Transit
Level Up Your Data Protection!
Explore How Testenium
Guarantees Data Privacy!


How Can Your Data Stay Secure Against Future Quantum Computing Threats?
Testenium's encryption tool is designed to protect your data using advanced technology, keeping it safe even from future threats like quantum computing. By staying ahead of these risks, Testenium ensures that your information remains secure, giving you peace of mind.
While traditional encryption methods may struggle with future advancements in quantum computing, Testenium uses special cryptographic algorithms that are resistant to such threats, ensuring that your documents stay safe in the long run.


Frustrations
Resolved by TESTENIUM
Ready to Get Started?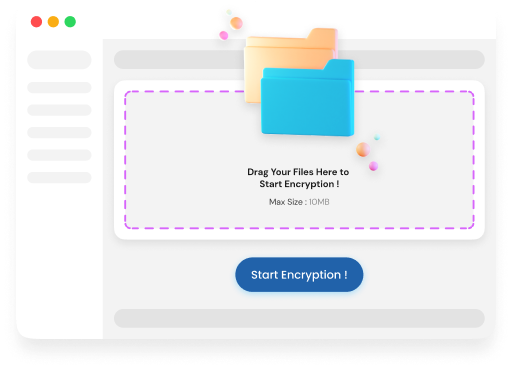
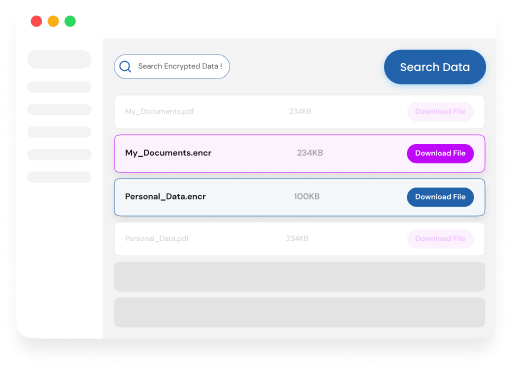
Encryption Process
Decryption Process
Access Encryption MenuNavigate to the Encryption menu within the TESTENIUM platform.
Select DocumentChoose the document or file you want to encrypt for protection.
Upload FilesUpload the selected files to the platform for encryption.
Pick recipientsDesignates recipients for the encrypted document with a simple click.
Automated Key GenerationThe chosen document undergoes robust encryption via 3 QRNG seeds, creating individually secured copies for receivers; each in their dedicated folders.
Testenium Destroys the KeyOnce encryption is complete, Testenium promptly destroys the encryption keys, leaving no room for unauthorized access.




Standardizing Encryption for Today & Tomorrow
With Testenium's Secure Encryption Practices !
Testenium takes a
multi-layered approach
to ensure your information remains protected.
This includes utilizing
industry best practices
and standards for encryption.
Standardizing 01
The Industry Standard: Advanced Encryption Standard (AES) with a Quantum LeapCurrently industry relies on the Advanced Encryption Standard (AES) to safeguard information at rest. This powerful method scrambles your data, making it unreadable for anyone without the decryption key. Testenium leverages the widely trusted AES-256 standard, but we go a step further. By incorporating Quantum-Resistant Key Generation Technology, Testenium ensures your data remains secure even with the potential advancements in quantum computing.
Standardizing 02
Quantum-Ready Encryption for a Secure TomorrowThe rise of quantum computers could potentially break traditional encryption methods. Testenium takes a proactive approach by incorporating Quantum-Resistant Key Generation Technology. This cutting-edge technology generates unpredictable keys that are virtually impossible to crack, even by powerful quantum computers. Testenium ensures your data remains protected not just today, but well into the future.
Standardizing 03
Staying Compliant: Encryption and RegulationsData security goes beyond technical measures. Regulations like GDPR, CCPA, and HIPAA set specific standards for data protection. Testenium understands the importance of compliance and ensures its encryption practices meet these regulatory requirements. This gives you peace of mind, knowing your data is secure and handled according to the law.
Standardizing 04
The Key to Security: Secure Key ManagementStrong encryption is only as effective as its key management practices. Testenium prioritizes secure key generation using Quantum Random Number Generators (QRNG). These unpredictable seeds create unique encryption keys that are impossible to guess, even for sophisticated computers. Additionally, Testenium eliminates the risk of key theft by destroying them immediately after use. Decryption utilizes the original seeds, ensuring a secure and keyless process.
Standardizing 05
Symmetric Encryption: Streamlining SecurityTestenium utilizes symmetric key encryption for its simplicity and efficiency. This method uses a single key for both encryption and decryption, streamlining the process. This eliminates the need for complex key management procedures associated with public key infrastructure (PKI) systems, offering a user-friendly and secure solution for data protection.
Got Questions?
Get Answers: Explore Our Encryption FAQ
Is Testenium's Encryption tool suitable for enterprise use?
Yes, Testenium's Encryption tool is designed for enterprise use, offering robust security features that scale with the needs of large organizations to protect sensitive data.
How does Testenium's Encryption tool ensure data accessibility & usability?
Testenium's Encryption tool ensures data accessibility by using virtual encryption keys that can be managed and accessed securely, maintaining data usability without compromising security.
How does Testenium's Encryption tool work?
Testenium's Encryption tool works by using advanced encryption algorithms to encode data, providing secure storage and transmission capabilities, and employing virtual keys for secure decryption when authorized.
What encryption algorithms does Testenium use to secure data?
Testenium uses industry-standard encryption algorithms, including AES-256 for robust security and protection against modern cryptographic attacks.
Can Testenium's Encryption solution be integrated with existing systems?
Yes, Testenium's encryption solution can be seamlessly integrated with existing systems, enhancing security without disrupting existing workflows.
Is Testenium compliant with data protection regulations such as GDPR and HIPAA?
Yes, Testenium is designed to comply with major data protection regulations like GDPR and HIPAA, ensuring that it meets legal requirements for data privacy and security.
How can I get started with Testenium's Encryption solution?
To get started with Testenium's Encryption solution, you can contact our support team for a demo and setup instructions, or visit our website to sign up for services or request more detailed information about deployment.
Company registered in England & Wales,
Registration # 09367824 | Privacy and Cookies Policy
177 Robin Hood Way, London SW15 3QG, United Kingdom
Registration # 09367824 | Privacy and Cookies Policy
177 Robin Hood Way, London SW15 3QG, United Kingdom
Designed and Developed by
Upview Technologies.
Upview Technologies.